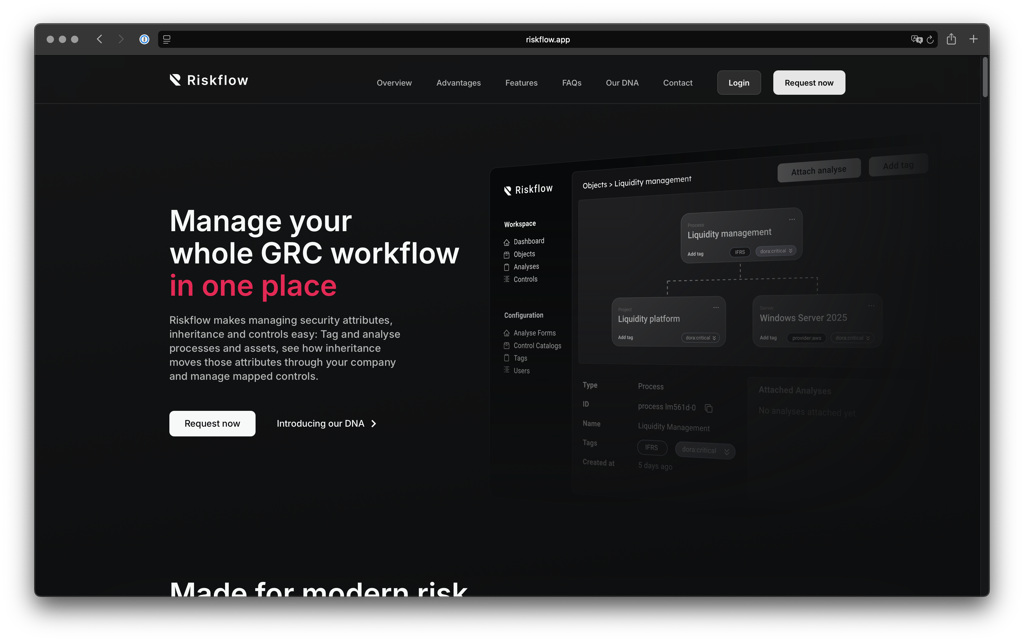
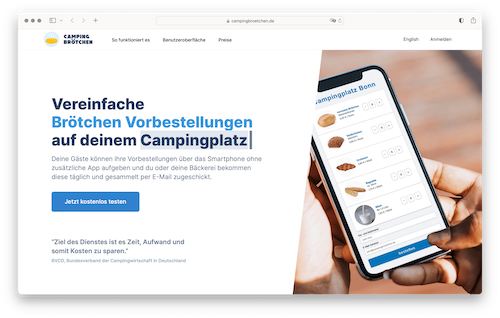
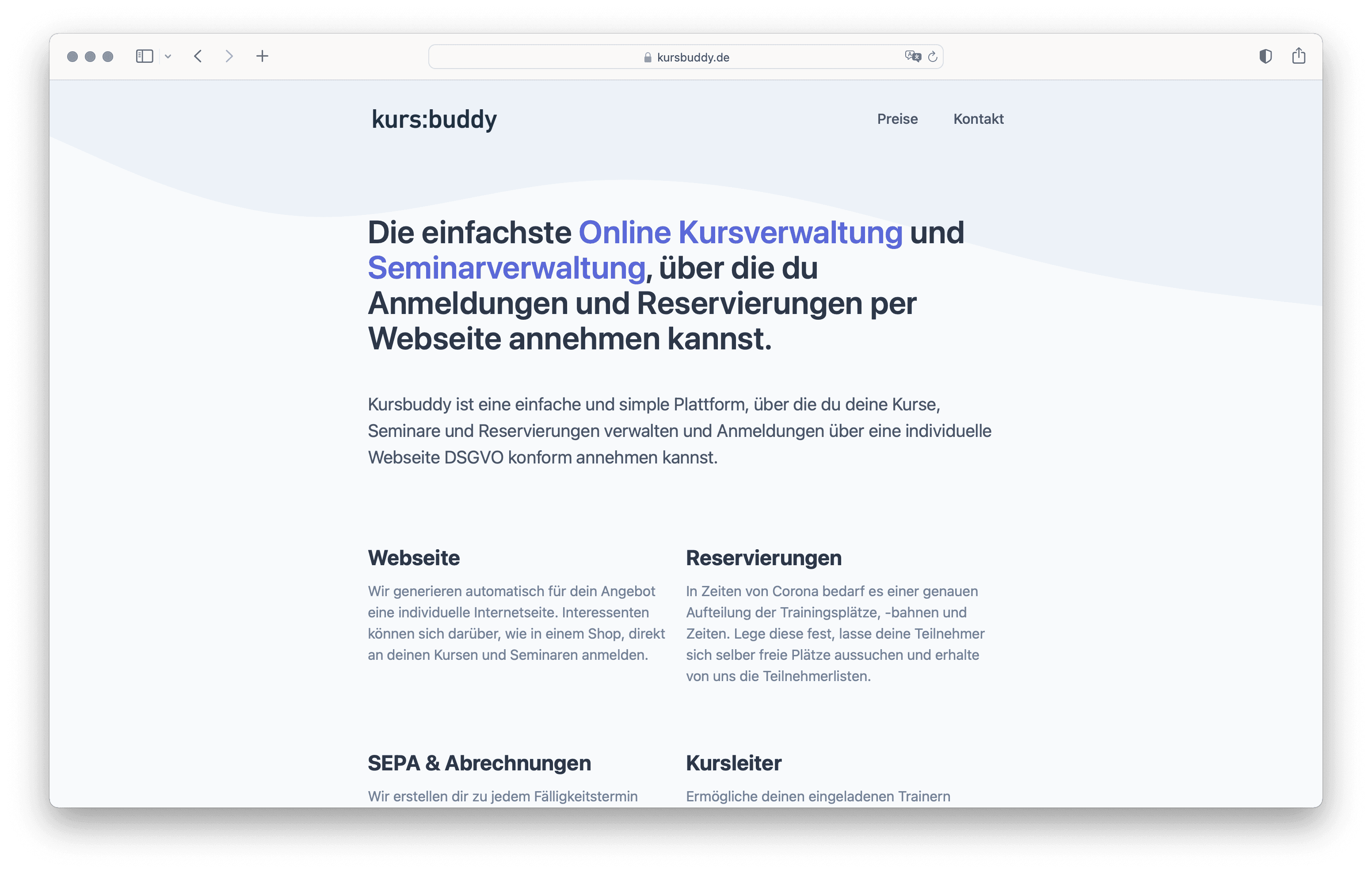
Hey! I'm Robin.
I'm a deeply technical software engineer and security expert, currently self-employed, previously worked as a red teamer & pentester at Deutsche Telekom AG.
- Automations and integrations
- Full-stack web applications
- Cloud solutions (with AWS)
- Security tools and infrastructure
- Penetration testing and red teaming
- Source code auditing
I strive for simplicity and quality.
Mostly writing Go, Elixir and JavaScript.
3x AWS certified and
2x Offensive Security certified.
open source
pgjobs
go
postgres job queue blueprint
tevents
go
private event logger and job monitor for tailnets
webanalyze
go
uncovers technologies used on websites
hntr
go nextjs
collaborative workspaces for recon data
smbwatch
go
fast samba fileshare indexing
wonitor
go
fast, zero config web endpoint change monitor
pipers
go
task automation framework
redAsset
go
subdomain enumeration by parsing FDNS dumps and CA transparency logs
gxss
go
blind XSS service alerting over slack or email