CVE-2016-5195 (Dirtycow) Local Root PoC
After the proof of concept code for CVE-2016-5195 (DirtyCow) was released, the game was on to ‘weaponize’ this PoC to a full local root privilege escalation. Because this bug was not that complicated, I began working on a simple modified version which is able to spawn a root shell.
My initial idea was something like this:
- Get the size of a SUID binary and make a backup.
- Overwrite this binary with a simple shell (ELF file) plus padding (so it’s the same size as the SUID binary).
- Execute our new shell.
After some trial and error I got stable version on some systems, however on a few others the kernel crashes after some seconds. I was not able to fix this, maybe someone else can achieve it with a different technique. There is a list of a few more PoC’s available on the official DirtyCow repository (yeah, mine is also there).
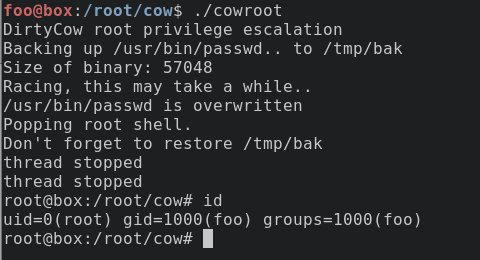
Hint: After getting a shell, doing echo 0 > /proc/sys/vm/dirty_writeback_centisecs may make the system more stable.
You can view my proof of concept here: https://gist.github.com/rverton/e9d4ff65d703a9084e85fa9df083c679