EPLUS Group (mobile network operator) security issue (SMS flood, MSISDN verification)
Some months ago (16th of Sep.) I found a security issue on an EPLUS service page, which allows you to send as much SMS as you want to their customers (only numbers from the EPLUS group are affected) with a special message.
During my tests I found that the only limit you are faced with in sending SMS is the bandwidth of your connection/their server. The SMS is send by a service hotline number and can not be traced back to you. The SMS-sending is triggered by a simple GET-request to their server.
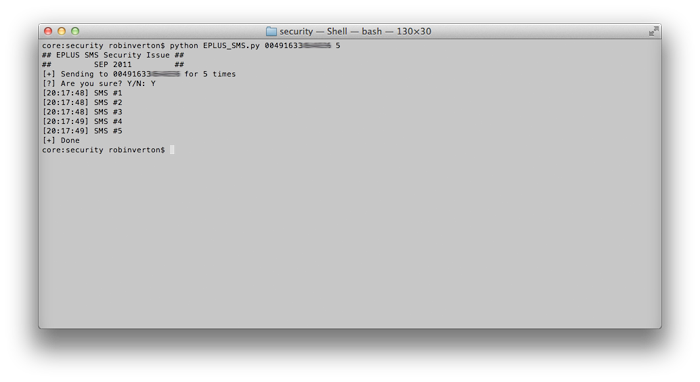
Because I could not find any suitable address for security related issues (or in other words: sadly there is no address for topics like this), I had to write several emails to their customer support to get an response so my findings were forwarded.
A few weeks later I received a phone call from a member of their technical service. He told me that I was absolutely right and that they are going to have a closer look on my findings. Two months have passed now, and except of a 5€ gift card I received (wow!), nothing happened. I will keep an eye on this and post additional informations on this issue when their team released a fix.
For the sake of completeness I also found a XSS vulnerability on their page. To make sure I will not overload their technical team with work I will wait to send this issue until they fixed the first one :]
Update: It is also possible to figure out if a given mobile number (MSISDN) inside the eplus network is valid or not. This is a big issue because spammers can guess all possible variations of mobile numbers, check if they are valid and make a list of correct numbers. (Note: According to wikipedia, the eplus group has about 22.1 million subscribers!)